Previously, we’ve written about the zero trust network security framework and separately, about...
Zero Trust Security: Never Trust and ALWAYS Verify
Although the phrase, “Trust, but verify” is frequently attributed to former US President Ronald Reagan, who used it on multiple occasions in the context of mid 80’s nuclear disarmament discussions with the then-Soviet Union; the quote was originally a rhyming Russian proverb, Доверяй, но проверяй (tr. Doveryay, no proveryay).

In fact, the core sentiments of the phrase are rather ironically attributed to the writings of Vladimir Lenin and Joseph Stalin, many years prior to the Geneva Summit.
In response to Reagan’s “trust” remarks during these now historic talks, Reagan’s counterpart, General Secretary Mikhail Gorbachev is said to have frequently quoted Ralph Waldo Emerson, saying, “the reward of a thing well done is to have done it.”
Speaking of trust, when it comes to cyber security, organizations across the globe are increasingly understanding the reality that trust is a massive vulnerability. As a result, a zero trust security model is rapidly becoming the security posture of choice (and necessity) for organizations, agencies, and businesses of all shapes and sizes. In fact, were Reagan still alive, one can imagine that he might apply a juxtaposed, “Never trust, and always verify” sentiment to the cyber security challenges we face today.
But what is zero trust (ZT)? Why is the security model backed and utilized by information industry titans including Microsoft and Google? Why has the US Government recently announced a federal strategy of zero trust in order to reduce the risk of successful cyber attacks against the Federal Government’s digital infrastructure? And what does all of this mean for your organization?
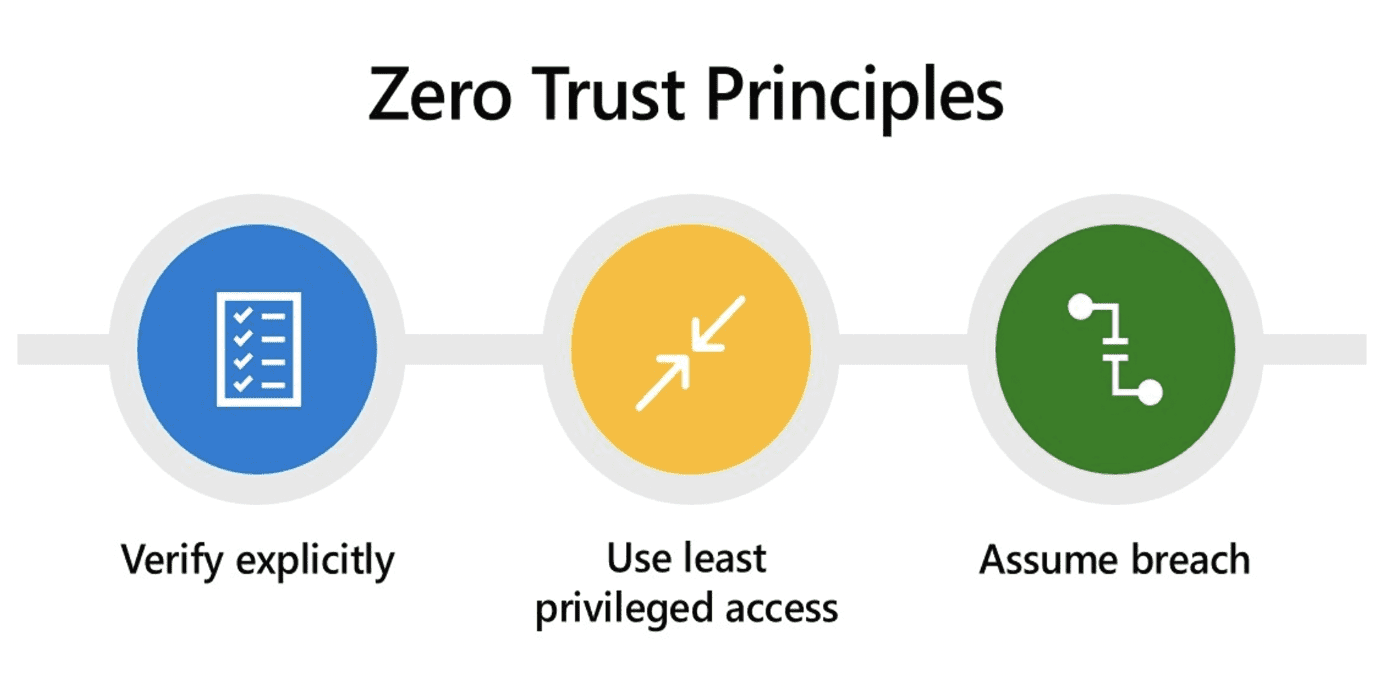
Zero Trust Principles
(source: Microsoft)
In essence, zero trust operates on the assumption that threats, both outside and inside the network, are an ever-present reality. Furthermore, it acknowledges that potentially every user and every device has already been compromised. To say this in a different way, instead of assuming everything behind the corporate firewall is safe, breach is assumed in the ZT model, and accordingly, verifies each request as though it originates from an open network.
The ZT security model treats every attempt to access the network or an application, as a threat. Instead of trying to secure perimeters, ZT assumes that the legacy “walled fortress” security approaches of days past have failed and that systems have already been breached. In response, rich intelligence and analytics resources are utilized to detect and respond to anomalies in real time, as the ZT model seeks to lessen the damage that can be caused within this compromised environment.
Additionally, because ZT operates under the premise that ALL networks are insecure, the ZT methodology individually evaluates each resource continuously to determine who is allowed access. Explicit verification is done every time a user seeks access to a component of the network, thereby ensuring that users are only accessing approved resources. This foundational element of continuous verification is instrumental in denying attackers room to maneuver, both inside and outside the ZT environment.
Again, what’s particularly noteworthy with the ZT security model is the significant shift in the overall philosophy of how data, networks and infrastructure are secured. The notion of verifying once, at the perimeter of the “walled fortress” environment, has been replaced by the philosophy that secure connectivity can only be achieved by eliminating transitive trust and continuously identifying and authenticating every device, user and identity before providing them with access…essentially continual verification of each user, each device, each application, and each transaction.
If the ZT model sounds like an over-reaction to current events, consider that the model itself has been around for quite a while…in fact, it was originally outlined in 2009 by Forrester’s John Kindervag. But part of what’s held it back prior to 2020, as Forrester’s own Chase Cunnigham recently pointed out is that, “ZT is prone to misconceptions. IT and business leaders often think that ZT is too hard and too expensive or that it requires them to restructure everything they’ve built or deploy next-generation firewalls everywhere. Because “trust everything” is easier to grasp than the ZT principle of “never trust, always verify,” ZT myths abound.”
Why You Should Care About Zero Trust
First, ZT isn’t a fad or a gimmick and, myths be danged, it *isn’t* going away. With critical infrastructure, supply chain, and valuable data under constant assault by cyber criminals and nation-state actors, it is clear that current legacy-based security infrastructure, software, and protocols are wholly insufficient.
On January 26, 2022, the Office of Management and Budget (OMB) announced a formal, federal strategy to move the U.S. Government toward a “zero trust” approach to cyber security. In the announcement, acting OMB Director Shalanda Young shared, “this zero trust strategy is about ensuring the Federal Government leads by example, and it marks another key milestone in our efforts to repel attacks from those who would do the United States harm.”
ZT is also one of the pillars of Google’s recently announced $10 billion investment to strengthen cyber security. Additionally, Microsoft has fully embraced the ZT model as paramount to its security future and integral to its focus on six key areas of defense: identities, endpoints, apps, data, infrastructure, and network. Microsoft has further suggested, based on sponsored research, that organizations implementing a ZT architecture through Microsoft’s solutions can realize ROIs exceeding 90%.
ACP CreativIT, Camera Corner Connecting Point, and Citon’s managed service customers benefit from a holistic, consistent, fluid, and dynamic platform which draws on best-in-class security technologies. These services, which incorporate multiple aspects of the zero trust security model, include backup system management, firewall management, server and network management, endpoint detection and response, enhanced network monitoring, multi-factor authentication, and more.
Additionally, our security, engineering, and support teams continually monitor for gaps, vulnerabilities, opportunities, and advancements and share these insights with our managed service customers.
In a zero trust cyber security world, we’re proud of the personal and professional trust we’ve earned from our clients. We’d love the chance to earn yours, too. Talk to one of our experts today at contactus@cccp.com.